分享 請 Linode 用戶注意,緊急情況。
http://slashdot.org/firehose.pl?op=view&type=submission&id=2603667
駭客聲稱已經取得 Linode 所有信用卡信息。
有卡號在上面的請關注信用卡使用情況,或者直接換卡。我已經 order 了 replacement card .
附駭客 irc 聊天記錄 以及證據截圖。
Linode 居然把加密信用卡使用的公鑰和私鑰放在了一起,簡直是....... 傻 X 都不足以形容!
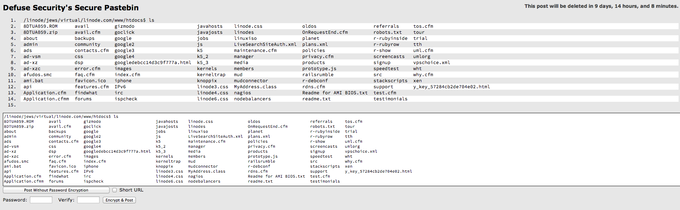
This is an edited version of the linode.log file for 15th April.
'ryan_' is involved with HTP (a computer cracking collective).
TL;DR version:
05:10 < ryan_> https://bin.defuse.ca/hq0Ay8RzpKdR6vQwYxnmhc
05:11 < ryan_> if that's not proof I don't know what is
If you are a linode customer, I strongly suggest reconsidering. And
changing your banking credentials.
* * *
05:05 < ryan_> Hey I can tell you
05:05 < ryan_> exact details of the attack
05:05 < ryan_> manager.linode.com was breached with a coldfusion exploit
05:05 < ryan_> it was compromised for a couple of weeks
05:05 < kyhwana> I hope they're using bcrypt/similar, etc.
05:05 < ryan_> we made a deal with linode staff not to share it
05:05 < ryan_> kyhwana: sha256crypt
05:05 < kyhwana> ryan_: god some proof?
05:05 < shmoon> "we"?
05:05 < kyhwana> s/d/t
05:05 < kyhwana> heh
05:05 < ryan_> they contacted law enforcement
05:05 < ryan_> broke the deal
05:05 < ryan_> kyhwana: the released database should serve as proof
05:06 < ryan_> We will also release the logs of the linode staff who participated in this deal
05:06 < shmoon> "WE"???
05:06 < shmoon> who is we?
05:06 < ryan_> of course they wouldn't have ever told you (customers) about it if we didn't tell them that we will release the data after we saw them contacting LE
05:06 < ryan_> does it matter who is "we"?
05:06 < ryan_> It's an entity I represent
05:07 < drclawski> of course it matters who you represent
05:07 < ryan_> you probably weren't targetted but doesn't stop us from releasing your credit card info since linode staff tried to fuck us over
05:07 < shmoon> hm
05:08 < drclawski> well, the way you talk right now I'm glad linode contacted law enforcement
05:08 < shmoon> :D
05:08 < gerryvdm_mbp> ah, could change back to my original password after intermediary one!
05:08 < Ruchira_> ryan_: got a link to that db where I can download it?
05:08 < Ruchira_> :*
05:08 < kyhwana> link 2 pastebin plz
05:09 < ryan_> Ruchira_: not yet
05:09 < mestri> this sounds so fishy
05:09 < shmoon> credit card details were leaked ? :o
05:09 < chesty> full of it
05:09 < ryan_> https://twitter.com/hacktheplanet
05:09 < ryan_> you can follow there
05:10 < ryan_> hey
05:10 < ryan_> lets prove it this way
05:10 < chesty> there's nothing there
05:10 < Ruchira_> ryan_: gimme the db or GTFO
05:10 < ryan_> https://bin.defuse.ca/hq0Ay8RzpKdR6vQwYxnmhc
05:11 < ryan_> if that's not proof I don't know what is
05:12 < mestri> hm i see.
05:12 < Ruchira_> wow someone can right click and view source O_o
05:12 < ryan_> Ruchira_: do you have the slightest idea on what you are talking about?
05:12 < Ruchira_> yup
05:12 < ryan_> well then, I wouldn't have the source code of any of those files, right?
05:13 < ryan_> and why would I have the y_key_57284cb2de704e02.html file name?
05:13 < ryan_> caker:{SHA}f6gtSn8vrtJfOr5BL73qur9pZjM=
05:13 < ryan_> mgreb:{SHA}Rs6+t2AmP8Zk9Tt2L8V6KoF/p68=
05:13 < ryan_> tasaro:{SHA}VX3HOGFij2T+vBPQsJziNeFih9s=
05:13 < ryan_> restelow:kO8AB7F2vGeTY
05:13 < ryan_> irgeek:{SHA}vB9kanV+A2b6YBHskkgrWPmDLhU=
05:13 < ryan_> sschwertly:{SHA}MhAwd561ZtgAH2NgXLltvmWlgfQ=
05:13 < ryan_> dariti:{SHA}qWfPCORks8jobCzOHX6BcX5FS+Q=
05:13 < ryan_> bkaplan:{SHA}npf7EGrBJVP/L70h830WZcjBMP8=
05:13 < ryan_> psandin:{SHA}tKrcBAD/mj25kX0MSrZKtWAbpRk=
05:13 < kyhwana> why would there be random AMI bios ROMS in that htdoc?
05:13 < ryan_> afolson:{SHA}udkD+S5jcqr66VDf6OgSxhHhbzQ=
05:13 < ryan_> cron:{SHA}FFwIAcaqmbdxfVGfpoCtd4pva4Y=
05:13 < ryan_> I wouldn't have those either
05:14 < ryan_> I don't know
05:14 < scottymeuk> kyhwana: even linode has random shit lying around like the rest of us :P
05:14 < ryan_> ask linode staff
05:18 < ryan_> kyhwana: I just pasted admin hashes
05:18 < ryan_> that should be enough
05:19 < ryan_> and manager is on the same box as the main website
05:19 < kyhwana> So what? anyone can make up hashes
05:19 < ryan_> See http://www1.linode.com/manager/
05:19 < AlexC_> The best thing to do is to wait for an official response from Linode, a follow up to their blog post
05:19 < ryan_> kyhwana: yes and I can get all the files in their wwwroot?
05:19 < ryan_> give me a name of a file which source you want
05:21 -!- mode/#linode [+b *!*[email protected].*] by akerl
05:21 -!- mode/#linode [+ntc ] by ChanServ
05:21 -!- ryan_ was kicked from #linode by akerl [ryan_]
05:22 < akerl> Sorry, I was busy nomming
05:24 -!- ssthormess [[email protected]] has joined #linode
05:24 < kyhwana> well, LEO involvement just imply CC breaches. If there's any chance of a CC breach, i'd like to know so I can change my CC number
05:24 < AlexC_> chesty: If they don't, they're stupid (and I don't like using that word to describe Linode after being with them for years!)
05:24 -!- ryan| [[email protected]] has joined #linode
05:24 < ryan|> quite rude of you
05:24 < Ruchira_> hi ryan!:
05:24 -!- azizur [[email protected]] has joined #linode
05:24 -!- mode/#linode [+b *!*@37.235.49.*] by akerl
05:25 < ssthormess> anyone works for linode here?
05:25 -!- ryan| was kicked from #linode by akerl [ryan|]
05:25 < chesty> and the cover up begins
05:27 -!- root__ [[email protected]] has joined #linode
05:27 -!- root__ is now known as ryan||
05:27 < chesty> http://seclists.org/nmap-dev/2013/q2/3
05:27 < ryan||> Quite rude out of you
05:27 < ryan||> To ban me like that
05:28 < ryan||> akerl: Mind sharing what motivated your bans on me?
05:28 < ryan||> Did I offend you by sharing the truth?
05:29 < ryan||> Hey, you didn't go by our deal. What did you expect?
05:30 < ryan||> I had a nice deal with linode staff that they don't share the fact htat they got owned with anyone and we won't release info on their hack
05:30 < ryan||> (including customer credit cards)
05:30 < ryan||> which will now be released
05:30 < AlexC_> ryan||: This is best sorted between you and Linode, if you could just let this channel get on to normalilty and support users that'd be great
05:31 < ryan||> AlexC_: oh, but it's users data at stake here
05:31 < scottymeuk> ryan||: if your going to release it, then why are you here? Nothing we can do to stop you.
05:31 < ryan||> scottymeuk: why can't I stop by and talk
05:31 < ryan||> Is that illegal?
05:32 < ryan||> ssthormess: you don't care about the fact that it took linode staff about two weeks to tell their customers about the breach?
05:33 < ssthormess> ryanll: no. I work with Citibank Chase and Bank of America and all three have zero customer liability.
05:33 < Ruchira> ryan||: give us the link to cold fusion vulnerability that you are talking about
05:34 < ryan||> Ruchira: 0day
05:34 < ryan||> linode staff apparently failed to deduce it themselves and relied on chmodding CFIDE to 000
05:36 < ryan||> (It's surprising that anyone is still running coldfusion, that's like connection a windows 98 box to the internet without a firewall)
05:36 < ryan||> ssthormess: did you reset your instance api keys?
05:36 < ryan||> lish keys too?
05:36 < ssthormess> ryanll: how I do that?
05:37 < ryan||> Do you care about your data integrity?
05:37 < ryan||> would you mind if your linode was hacked?
05:37 < kyhwana> ohnoes, you have a public key!
05:37 < ryan||> kyhwana: lish passwords were stored in plain text
05:38 < ryan||> Last time I checked you couldn't disable password authnetication
05:38 < ryan||> and linode staff didn't properly secure the screen setup lish uses so it allowed breaking out of lish to the host environment
05:38 < ryan||> so someone using the same node as you being compromised would be enough for your server to be compromised
05:38 < kyhwana> and who leaves a login into their box logged in on lish eh?
05:38 < ryan||> Does it matter when you can break out to the host environment?
05:39 < ryan||> And unless you changed your api key, someone can just change your boot configs to init=/bin/bash
05:40 < gerryvdm_mbp> lish passwords were saved in plaintext?
05:40 < ryan||> Yep
05:40 < ryan||> so were the api keys (which could at least have been hashed)
05:42 < ryan||> credit cards were encrypted, sadly both the private and public keys were stored on the webserver so that provides 0 additional security
05:42 < AlexC_> If this is true, which I'm guessing it is, it's like finding out a good friend of many years has betrayed you :P I deeply hope that Linode provide full transparency on this
05:42 < gerryvdm_mbp> are they hashed now?
05:42 < ryan||> AlexC_: did they provide any transparency on the previous hacks?
05:42 < ryan||> gerryvdm_mbp: probably not
05:43 < AlexC_> ryan||: Not entirely, which was just wonderful
05:43 < ryan||> I don't know, but seeing how long it took for linode staff to detect us. I doubt it
05:43 < gerryvdm_mbp> i can understand php script kiddies storing passwords as plaintext, but a hoster.... that would be quite shocking
05:43 < AlexC_> But if they don't give details this time, they are going to have to do something incredilble to keep me as a customer
05:43 < ryan||> Well linode also had terribly configured coldfusion
05:43 < Ruchira> ryan||: I dont think linode would ever store lish passwords on plain text.
05:44 < ryan||> (adobe manuals tell you to not allow public access to /CFIDE/, which linode did)
05:44 < ryan||> Ruchira: oh but they did
05:44 < gerryvdm_mbp> ryan|| how do you know this?
05:44 < scottymeuk> gerryvdm_mbp: im pretty sure its one of the first things even script kiddles learn :P
05:44 < ryan||> Because I'm one of the people who hacked it?
05:44 < Ruchira> ryan||: proof?
05:45 < gerryvdm_mbp> you cant be a professional and not knowing how even hashing with salts is such a bad idea, but plaintext... that would be several levels of incompetence
05:45 < ryan||> The zine is scheluded to be released on the first of may which will contain the full database
05:45 < ryan||> Ruchira: I can get you the source code of the script that stores lish passwords
05:45 < ryan||> sec
05:45 < d-b> ryan||: which zine?
05:45 < ryan||> let me find it, coldfusion is horrible to read
05:45 < ryan||> d-b: htp5
05:47 < Ruchira> ryan||: first of the may? why?
05:47 < ryan||> Ruchira: due to other content
05:48 -!- ryan|| [[email protected]] has quit [autokilled: This host violated network policy. Mail [email protected] if you think this in error. (2013-04-15 09:48:28)]
05:48 < chesty> how has he violated network policy?
05:48 < shmoon> even i am wondering
05:49 < kyhwana> hacked box, obviously
05:49 < scottymeuk> Because they want to try and hide it?
05:49 < AlexC_> Not cool Linode, not cool
05:49 < shmoon> man even i am afraid now :S
05:49 -!- ryann [[email protected]] has joined #linode
05:49 < Ruchira> wow :D
05:49 < ryann> Why are people so rude nowadays
05:49 < ryann> glining me like that and stuff
05:49 < ryann> Well akilling, little difference
05:50 < chesty> someone doesn't want the truth to be known
05:50 < ryann> Generally having to ban users is a clear sign of incompetence by the staff
05:50 < AlexC_> Yep, which is *very* bad of Linode
05:51 < AlexC_> I understand they may not want someone to disclose details like this, but the details *need* to come out. If Linode don't do it them selves, then they are fools
05:51 < ryann> If linode had any way of proving that I'm not telling the truth they wouldn't be banning me
05:51 < ryann> they'd be calling me out
05:51 < chesty> ryann: so my linode has FDE, do you need to reboot in order to break in?
05:51 < Ruchira> all the staff should be eyeing on this chat right now lol
05:51 < mikegrb> lulz
05:51 < ryann> chesty, not necessary
05:52 < AlexC_> Ruchira: I assume due to the lack of their presence, they are all huddled around a table discussing this
05:52 < ryann> FDE will make it significantly harder, but you can still access the memory while it's running
05:52 < rww> except for mikegrb, who is dilligently sitting here typing "lulz" every so often
05:52 < rww> (yes, I know)
05:53 < chesty> ah well, i made it harder, so I'm happy
05:53 < ryann> btw
05:53 < ryann> $dbhost = 'newnova.theshore.net';
05:53 < ryann> $dbname = 'linode_forums';
05:53 < ryann> $dbuser = 'linode';
05:53 < ryann> $dbpasswd = 'cfr41qa';
05:56 < ryann> gdi can't linode just use some normal language
05:56 < ryann> Their current source is horrible to read trough
05:56 < Ruchira> ryann: the shore was abandoned long time ago. Im wondering why would they use that host name for a db host
05:57 < ryann> Ruchira, the forum is pretty old too
05:57 < ryann> phpbb2
05:57 < ryann> <cfif ListLen(cgi.script_name, "/") gt 2 AND ListGetAt(cgi.script_name, 2, "/") eq "linode" AND NOT ListFind("index.cfm,linode_edit.cfm,linode_resize.cfm,label.cfm,cancel.cfm,dc_choose.cfm,su.cfm,pastdue.cfm", ListGetAt(cgi.script_name, 3, "/"))> <cfinclude template="/members/linode/common/dsp_topNav.cfm"> </cfif>
05:57 < ryann> this code
05:57 < ryann> It's so dirty I feel bad reading it
05:58 < AlexC_> ryann: People have been bugging them to upgrade the forums for a long time
05:59 < ryann> I like how linode does stuff like this
05:59 < ryann> manager/controllers/Signup.cfc: var lsd = query("getLinodeSignupData", "SELECT FieldName, Fieldvalue FROM ln_LinodeSignupData WHERE LinodeSignupID = #ls.LinodeSignupID#").recordSet;
05:59 < ryann> var lsd
06:00 < AlexC_> ryann: So, are you saying CC details have also been compromised?
06:00 < ryann> Yep
06:00 < AlexC_> ryann: And you plan on releasing these?
06:00 < ryann> They did try to encrypt them, but using public key encryption doesn't work if you have the public and private key in the same directory
06:00 < AlexC_> Oh linode
06:00 < shmoon> please dont get me wrong, can you hack someone's box here? so that its compeltely proved or something, i need to ge tback to work too. dont hack mine.
06:00 < ryann> AlexC_, probably. Linode didn't hold on to their part of the deal
06:01 < AlexC_> ryann: Sure, but there is no reason to compromise so many people
06:01 < Ruchira> ryann: money deal?
06:01 < ryann> Ruchira, "We won't share if you don't share"
06:02 < ryann> But they contacted law enforcement, we were monitoring their communications and caught onto that though
06:02 < Ruchira> so whats the point of hacking linode then?
06:02 < ryann> Access to a couple of clients
06:02 < ryann> nmap was just funny
06:02 < Ruchira> bitcoin?
06:02 < ryann> If I wanted bitcoins, I'd have went after softlayer and got mtgox
06:02 < ryann> But money's boring
06:03 < scottymeuk> Money is boring, i agree.
06:03 < gerryvdm_mbp> bitcoin is money?
06:03 < ryann> Well, it's not
06:03 < scottymeuk> gerryvdm_mbp: naa
06:04 < ryann> But what would you do with it besides exchange it to money?
06:04 < scottymeuk> ryann: try to buy a linode on IRC
06:04 < gerryvdm_mbp> store it :)
06:04 -!- ryann [[email protected]] has quit [Quit: CGI:IRC]
06:05 -!- ryannn [[email protected]] has joined #linode
06:05 -!- brennannovak [[email protected]] has joined #linode
06:05 < ryannn> Bitcoins are quite useless, and besides storing bitcoins after stealing everything from mtgox would be pointless
06:05 < Ruchira> ryannn: for what kind of "content" that you are waiting for?
06:05 < ryannn> as bitcoin prices would permanently crash as the last bits of trust are gone
06:06 < ryannn> Ruchira, other targets
06:06 < Ruchira> to release it on may 1
06:06 < gerryvdm_mbp> only use i can think of it is exchanging pure services :)
06:06 < gerryvdm_mbp> but then again its an unnecessary layer
06:06 < scottymeuk> gerryvdm_mbp: if it ever got mainstream, governments would find a way to control it anyway, so its pointless
06:07 < gerryvdm_mbp> its a scheme, it cant get mainstream
06:07 < ryannn> Bitcoins are mostly a lie anyways
06:07 < scottymeuk> Regardless, if it got 'big', they would find a way
06:07 < ryannn> They say there's no 'central weak point'
06:07 < ryannn> Yeah there is, there's the developers
06:08 < ryannn> There's been bugs in the client that have allowed the blockchain to split previously
06:08 < ryannn> One could just backdoor the bitcoin client binaries, not the source.
06:08 < ryannn> Nobody would figure it out until it's too late
06:10 < scottymeuk> Id rather a bank control my money, so that if it all goes fucked up, there is atleast someone to blame.
06:15 < gkmngrgn> hello, i forgot my password and linode's email reminder service doesn't work. i checked spam box but there's no email from linode.
06:15 < shmoon> ryannn: can you give him the password?
06:15 < scottymeuk> shmoon: damn you, you beat me to it!
06:23 < ryannn> shmoon, sorry I only have the sources on my server
06:23 < ryannn> db is on my desktop
06:24 < scottymeuk> ryannn: so your not in this to do large scale damage, only after a few clients?